Continuous Data Security to Protect Data Across Hybrid Workloads
Understand sensitive data to apply appropriate protection and deploy advanced early warning and threat detection mechanisms to protect data and AI pipelines proactively.


Overview video
Commvault Risk Governance
Advanced data governance capabilities coupled with proactive threat detection helps secure today’s cloud-first enterprises.
Data governance controls & threat and anomaly detection
Improve your data and cybersecurity posture by better understanding data and proactively monitoring for cyber threats like hackers, ransomware, and malware.
Discover, classify, and protect sensitive data
Reduce your data footprint and safeguard sensitive data to maintain trust, including secrets like keys or passwords, PII, and other sensitive or regulated data.
Reduce risk and improve cyber resilience
Added protection for applications and data, including proactive and in-line scanning of data for new and persistent threats, helps reduce risk of recovery failures.
Understand data and backup resiliency posture
Easily check configurations and settings within your data against best practices to reduce risk to your live and backup environments.
enhanced control
Advanced data governance
Commvault® Cloud provides visibility and control over your data estate with automated data governance policies that help reduce your attack surface and assist with regulatory compliance.

Scan and classify live data
Automatically label and tag data to apply retention and data protection policies.
Automate data lifecycle actions
Trigger retention policies based on your data lifecycle, or pause those policies indefinitely in the case of eDiscovery or legal holds.
Minimize redundant, obsolete, and trivial data
Shrink your attack surface and storage costs by eliminating duplicate, unnecessary, or unneeded data from your data estate.
Fully customizable data discovery
In addition to dozens of out-of-the-box classifiers for sensitive data, automatically discover anything your data governance teams deem sensitive—including keywords and secrets like API keys.
ADVANCED SECURITY & RISK MITIGATION
Early warning & threat and anomaly detection
Commvault Cloud helps shift your cyber defenses left to detect threats and mitigate risk earlier in the attack lifecycle.

Detect threats and unusual activity
Discover malware, automatically quarantine suspicious files, and create a clean point so that corrupt or compromised data isn’t restored during recovery.
Deploy decoys and traps for attackers
Strategically place high-value decoy data to look legitimate but act as an early warning sensor to detect threats proactively.
Implement continuous monitoring
Use sensors across your environment to detect nefarious network traffic or suspicious behavior, allowing your security operations teams to analyze security incidents.
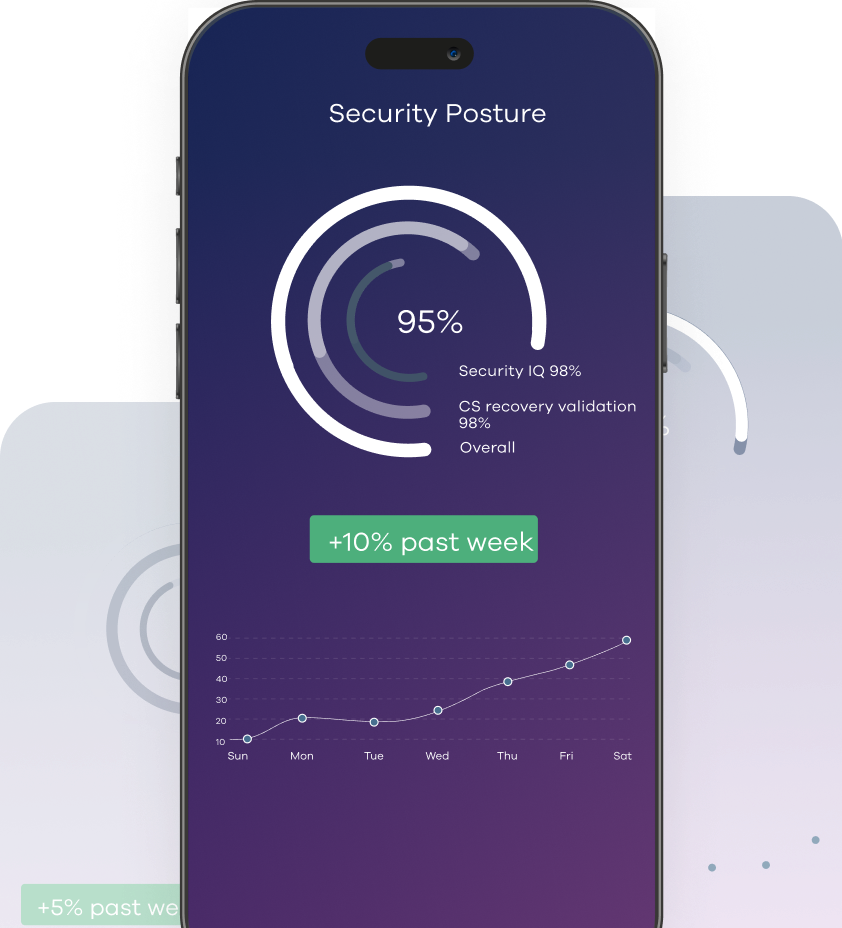
DATA SECURITY POSTURE MONITORING
Harden and safeguard data from internal and external threats
Reduce exposure, drive resilience, and organically improve your security posture.

Security control monitoring
Visualize the security posture of your environment with intuitive dashboards and reporting.
Evaluate configuration against best practice
Get intelligent recommendations to help improve your backup environment’s security posture based on industry best practices.
Advanced threat indicators
Quickly drill down into suspicious activity and investigate malware- or ransomware-infected files.

Analyst Report
Analyzing the Economic Benefits of Cyber Resilience with Commvault® Cloud
Commvault Cloud drives cost-efficiency, agility, and cyber resilience with lower TCO
Our Reach
Supporting more than 100,000 companies






related resources
Explore more platform resources

DATASHEET
Identify malware and prevent reinfection
with Commvault® Cloud: Threat Scan
Learn to enable swift and trusted data recovery by analyzing backup data to find encrypted and corrupted files.

SOLUTION BRIEF